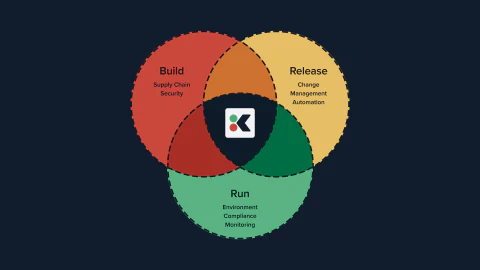
Software Bill of Materials (SBOMs) are crucial for maintaining software security and supply chain transparency. They provide a detailed list of all components, libraries, and dependencies within a software application, enabling organizations to identify and address potential vulnerabilities, license compliance issues, and other risks.
By generating and tracking SBOMs in Kosli, you can establish a centralized and auditable repository for your software’s supply chain information. This allows you to:
- *Track component provenance*: Understand the origin and history of each software component, ensuring that you’re using trusted and verified sources.
- *Identify vulnerabilities*: Quickly pinpoint and address any known security vulnerabilities within your software’s dependencies.
- *Manage license compliance*: Ensure that all components within your software comply with relevant licenses and avoid legal issues.
- *Improve incident response*: Streamline your response to security incidents by having a clear understanding of your software’s composition.
This post will guide you through the process of generating and tracking SBOM attestations using Kosli, helping you enhance your software security and supply chain transparency.
Creating a CycloneDX SBOM using Syft
Kosli can support various methods of SBOM creation. In this example we’ll show how to use syft to generate CycloneDX Software Bill of Materials (SBOMs).
First, we’ll use the syft command to generate a CycloneDX SBOM for the kosli cli tool:
# Use syft to generate a cyclonedx sbom and a text-table
# for the kosli binary
syft ./kosli --output cyclonedx-json=sbom-cyclonedx.json --output syft-table=sbom-table.txt
This command creates two files: sbom-cyclonedx.json containing the CycloneDX SBOM and sbom-table.txt containing a human-readable table of the SBOM contents.
Registering an Attestation Type for CycloneDX SBOMs in Kosli
In Kosli, you can store attestations either in generic untyped formats or as named types which are validated against a schema. Since we’d like to ensure the structure of this data, let’s go ahead and register a custom type to validate against a CycloneDX schema.
To do this, we’ll start by downloading the public CycloneDX schema:
# Download the cyclone-dx schema
curl -L -o bom-1.6.schema.json https://raw.githubusercontent.com/CycloneDX/specification/master/schema/bom-1.6.schema.json
Then we use the kosli cli to create a custom attestation type in Kosli using the downloaded schema:
# Create a custom attestation type in Kosli with the schema
kosli create attestation-type cyclone-dx-1-6 --schema bom-1.6.schema.json
Recording the SBOM Attestation in Kosli
Now, we’ll record attestations for the binary provenance for the artifact:
# Attest the binary provenance for the artifact
kosli attest artifact ./kosli \
--artifact-type file \
--build-url http://localhost \
--commit-url http://localhost/commit/$(git rev-parse HEAD) \
--flow demo-sbom-tracking \
--trail $(git rev-parse HEAD) \
--name binary
Finally, we’ll attest the SBOM to the trail under the artifact:
# Attest the sbom to the trail (under the artifact)
kosli attest custom \
--type cyclone-dx-1-6 \
--name binary.cyclone-dx-sbom \
--attestation-data sbom-cyclonedx.json \
--flow demo-sbom-tracking \
--trail $(git rev-parse HEAD) \
--attachments sbom-table.txt \
--artifact-type file ./kosli
This process records the SBOM and its associated metadata in Kosli, providing a traceable and auditable record of your software components. We’ve also uploaded the human readable sbom-table.txt as an attachment so that it can be viewed in the browser later.

(See it live: source)
Putting this into production
Now, typically you don’t want to be creating your SBOM’s on your local machine (in fact, this is a major no-no from a SLSA perspective). Instead, you’ll want to create these attestations in your secure build process in CI. We do this in github with the anchore sbom marketplace action and and the kosli cli marketplace action:
(source: github)